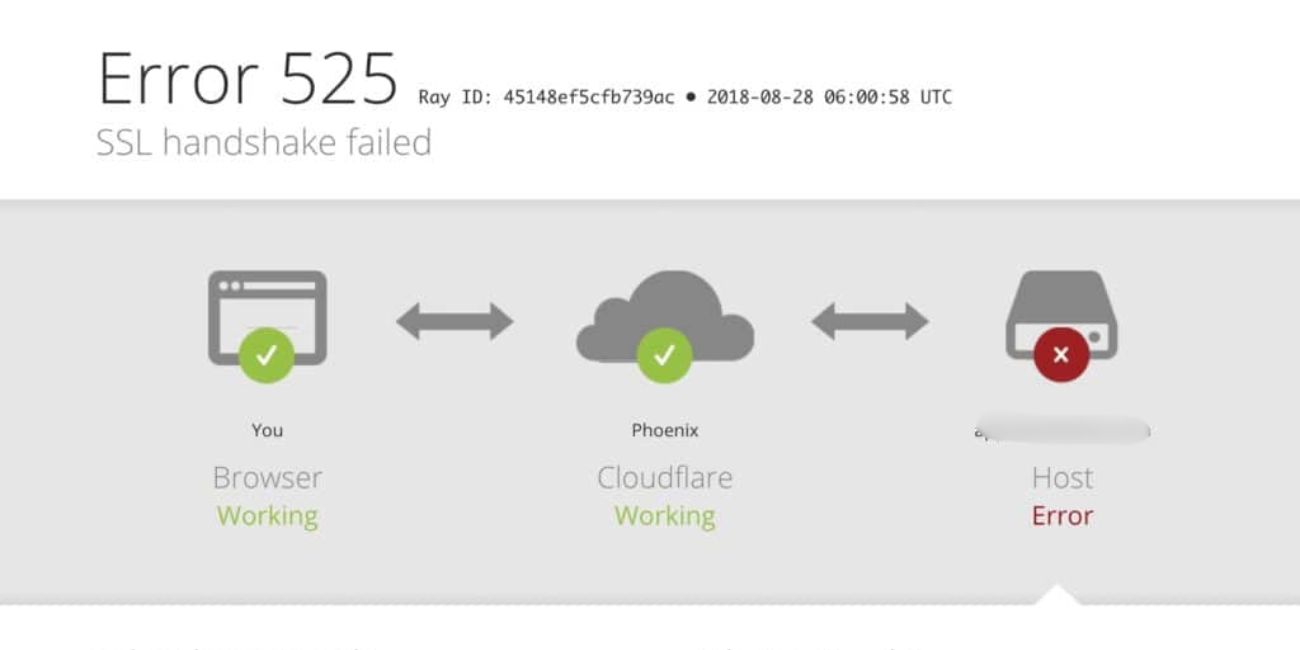
In today’s digitally connected ecosystem, the reliability and security of encrypted communications stand at the forefront of web performance and trust. Content delivery networks (CDNs) like StackPath play a crucial role in ensuring sites stay fast and secure. However, in early 2024, multiple services relying on StackPath experienced intermittent SSL handshake failures, causing disruptions across a variety of global web applications. At the root of these issues was the complex behavior of TLS renegotiation, a lesser-known aspect of secure web connections that, in certain configurations, led to instability.
TL;DR
Several services using StackPath experienced intermittent SSL handshake errors due to issues with TLS renegotiation. The instability was traced to incompatibilities between clients and StackPath edge configurations during the TLS handshake phase. Stabilization was achieved by implementing TLS version pinning, effectively reducing negotiation complexity and eliminating unexpected behavior. By locking supported versions, enterprises regained full control and predictability of secure communications.
Understanding the Problem: TLS Renegotiation
TLS (Transport Layer Security) is a protocol that enables secure communication over networks. During an HTTPS connection, an initial handshake negotiates keys, algorithms, and session characteristics. A feature of TLS is that this handshake can be renegotiated mid-session—for instance, to refresh session keys or alter security parameters. While flexible, this mechanism brings an overhead that can introduce errors, particularly when edge networks and clients have mismatched expectations.
StackPath’s infrastructure, designed for rapid scalability, uses high-performance SSL termination at network edges. Recently, changes to the way StackPath handled TLS 1.3 and fallback compatibility with older TLS versions created unexpected renegotiation behavior. As TLS has evolved over time, support for renegotiation has become increasingly fragmented. TLS 1.3, for instance, does not support renegotiation, making negotiation attempts not only unnecessary but problematic in mixed-environment connectivity.
The resulting behavior was characterized by:
- Handshake timeouts when connecting to StackPath-powered services
- Connection resets particularly in browsing sessions that lasted more than 5 minutes
- Inconsistent SSL errors depending on browser, client library, and device firmware
These symptoms were sporadic and difficult to reproduce, leading investigators to dig deep into packet captures and TLS debugging output.
Impact on the Web Ecosystem
The scope of the issue was initially hard to contain. High-availability platforms such as e-commerce storefronts, application APIs, and streaming services began reporting a rise in unexplained client-side SSL failures. In an edge environment where performance monitoring is often passive, the subtle nature of client-triggered renegotiation meant the problem flew under the radar for days.
Once identified as a renegotiation issue, affected parties noted that the failures were more common when clients used unpatched versions of OpenSSL or Java-based runtimes where renegotiation logic differed subtly from official TLS standards. Even updated browsers experienced handshake instability due to how aggressively they attempted to re-establish or resume sessions via 0-RTT or partial resumption techniques.
This incident brought to light how interoperability among cryptographic clients—and their assumptions—can cause unforeseen behavioral divergence. More critically, it highlighted the fragility created when highly abstracted cloud services handle security details behind the scenes.
The Root Cause: Protocol Mismatch and Expectation Drift
Investigation logs revealed that StackPath had updated part of its edge delivery software stack to optimize for TLS 1.3, including a more aggressive deprecation of legacy protocol features not included in the modern spec—such as renegotiation. In doing so, some edge points were silently rejecting mid-session renegotiation requests without proper completion of the TLS alert or response protocol.
Here’s what caused the issue to surface erratically:
- Client-side fallback mechanisms assumed renegotiation capability still existed
- Edge devices under certain latency conditions deviated from standard closure behavior
- Session resumption attempts mimicked renegotiation but failed under new rules
The combination of these behaviors resulted in sessions that either silently failed or produced generic SSL “bad record” errors. Responses varied based on code and library implementations, complicating detection.
Mitigation Strategy: TLS Version Pinning
To stabilize connections, StackPath engineering and impacted clients turned to a well-established technique: TLS version pinning. This involves configuring systems to support one or more specific versions of the TLS protocol—usually by explicitly specifying the highest mutually supported version.
By defining the exact version allowed (e.g., TLS 1.2 or TLS 1.3) rather than relying on protocol negotiation, all parties formed consistent expectations during the handshake. This action:
- Eliminated renegotiation attempts entirely on both server and client sides
- Reduced handshake time and packet overhead
- Resolved the subtle compatibility mismatches provoked by library assumptions
Enterprise system administrators applied version pinning policy-wise, often using tools such as:
- Cloudflare and StackPath TLS control panels to restrict SSL termination behavior
- Web server configurations (e.g., NGINX/OpenSSL flags) to enforce TLS version
- Client-side enforcement using Java security protocols or browser group policy templates

Ongoing Vigilance in TLS Environments
While TLS version pinning proved to be an effective stopgap—and in many cases a long-term solution—industry leaders advise caution. TLS is constantly evolving. Future browser updates or StackPath patches might quietly reintroduce similar negotiation edge cases if new features depend on handshake flexibility.
Organizations are encouraged to adopt proactive observability tools that analyze TLS sessions in real-time. These include:
- Full packet inspection and logging of TLS handshakes under test conditions
- Continuous compatibility testing using services like SSLLabs or hardened TLS scanners
- Regular audits of client software libraries handling encryption and renegotiation
It’s critical to recognize that what works in one environment may fail in another based on geography, CDN edge routing, or device type. Security protocols, while standardized, still leave enough room for environmental artifacts to cause functional anomalies.
Conclusion
The StackPath TLS renegotiation episode should serve as a cautionary tale for developers and infrastructure teams. Despite TLS being a mature and well-documented protocol family, the nuanced variations in client and server expectations—as highlighted here—can wreak havoc on availability and user trust.
Through TLS version pinning, impacted organizations were able to regain stability and avoid the latency and error-prone nature of mid-session renegotiations. However, long-term resilience requires a strategic combination of tight protocol compliance, client discipline, and continual observation of security layer behavior.
For CDN providers and cloud services, this incident casts a spotlight on the responsibility to communicate changes in protocol behavior clearly and ensure transparent control paths for customization. Ultimately, it reinforces an enduring principle of network security: stability depends as much on predictability as it does on encryption strength.